Jully 18, 2022
Rules for running functions after React Firebase getAuth()
When using React Firebase, it is important to understand the rules for running functions after getAuth(). GetAuth() is a function that is used to authenticate users and is a key component of React Firebase. In order to ensure that the authentication process is secure and efficient, there are certain rules and guidelines that must be followed when running functions after getAuth(). This essay will discuss the six main rules for running functions after getAuth() in React Firebase.
Rule #1: Use the correct authentication method
The first rule for running functions after getAuth() in React Firebase is to use the correct authentication method. Depending on the type of application being built, different authentication methods may be required. For example, if an application requires users to log in with their email and password, then the email/password authentication method should be used. Similarly, if an application requires users to log in with their social media accounts, then the social media authentication method should be used. It is important to use the correct authentication method in order to ensure that the authentication process is secure and efficient.
Rule #2: Check for errors
The second rule for running functions after getAuth() in React Firebase is to check for errors. When a user attempts to authenticate, it is important to check for any errors that may have occurred during the authentication process. This done by using the “catch” method in React Firebase. The “catch” method will catch any errors that occur during the authentication process and will allow the developer to handle them appropriately. By checking for errors, developers can ensure that the authentication process is secure and efficient.
Rule #3: Use secure passwords
The third rule for running functions after getAuth() in React Firebase is to use secure passwords. It is important to use strong passwords when authenticating users in order to ensure that their accounts are secure. Strong passwords should contain a combination of upper and lowercase letters, numbers, and special characters. Additionally, it is important to use different passwords for different accounts in order to further increase security. By using secure passwords, developers can ensure that the authentication process is secure and efficient.
Rule #4: Use two-factor authentication
The fourth rule for running functions after getAuth() in React Firebase is to use two-factor authentication. Two-factor authentication is an additional layer of security that requires users to enter a code sent to their phone or email address in order to authenticate. This additional layer of security helps to ensure that only authorized users are able to access an account. By using two-factor authentication, developers can ensure that the authentication process is secure and efficient.
Rule #5: Monitor user activity
The fifth rule for running functions after getAuth() in React Firebase is to monitor user activity. It is important to monitor user activity in order to detect any suspicious or unauthorized activity. This done by using the “onAuthStateChanged” method in React Firebase. The “onAuthStateChanged” method will allow developers to monitor user activity and detect any suspicious or unauthorized activity. By monitoring user activity, developers can ensure that the authentication process is secure and efficient.
Rule #6: Use encryption
The sixth rule for running functions after getAuth() in React Firebase is to use encryption. Encryption process that scrambles data so that it cannot be read by unauthorized users. It is important to use encryption when authenticating users in order to ensure that their data remains secure. By using encryption, developers can ensure that the authentication process is secure and efficient.
Conclusion:
In conclusion, there are six main rules for running functions after getAuth() in React Firebase. These rules include using the correct authentication method, checking for errors, using secure passwords, using two-factor authentication, monitoring user activity, and using encryption. By following these rules, developers can ensure that the authentication process is secure and efficient.
Recent Posts
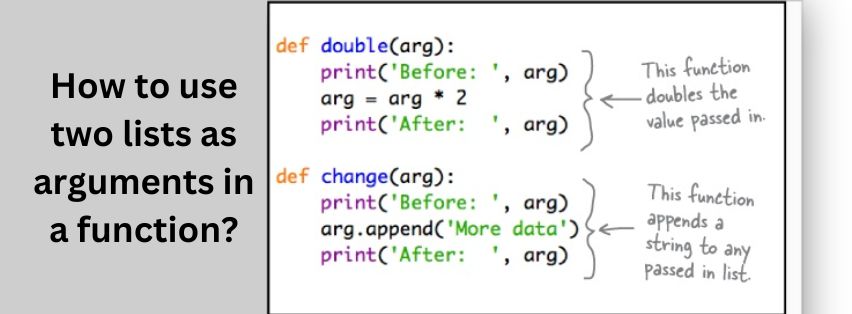
How to use two lists as arguments in a function?
Jully 11, 2022

Introduce the topic of booking systems in business.
Jully 11, 2022

Top 5 SEO plugins for wordpress.
Jully 11, 2022



